
Your Trusted Partner in IT Solutions.
"Delivering Tailored Services for Maximum Efficiency and Security"
Advanced Encryption Techniques
Our encryption solutions ensure that your data is securely encrypted both at rest and in transit, safeguarding it from unauthorized access.
- Data Encryption: Implement industry-standard encryption algorithms to protect sensitive information.
- Secure Communication: Use encryption protocols for secure communication channels.
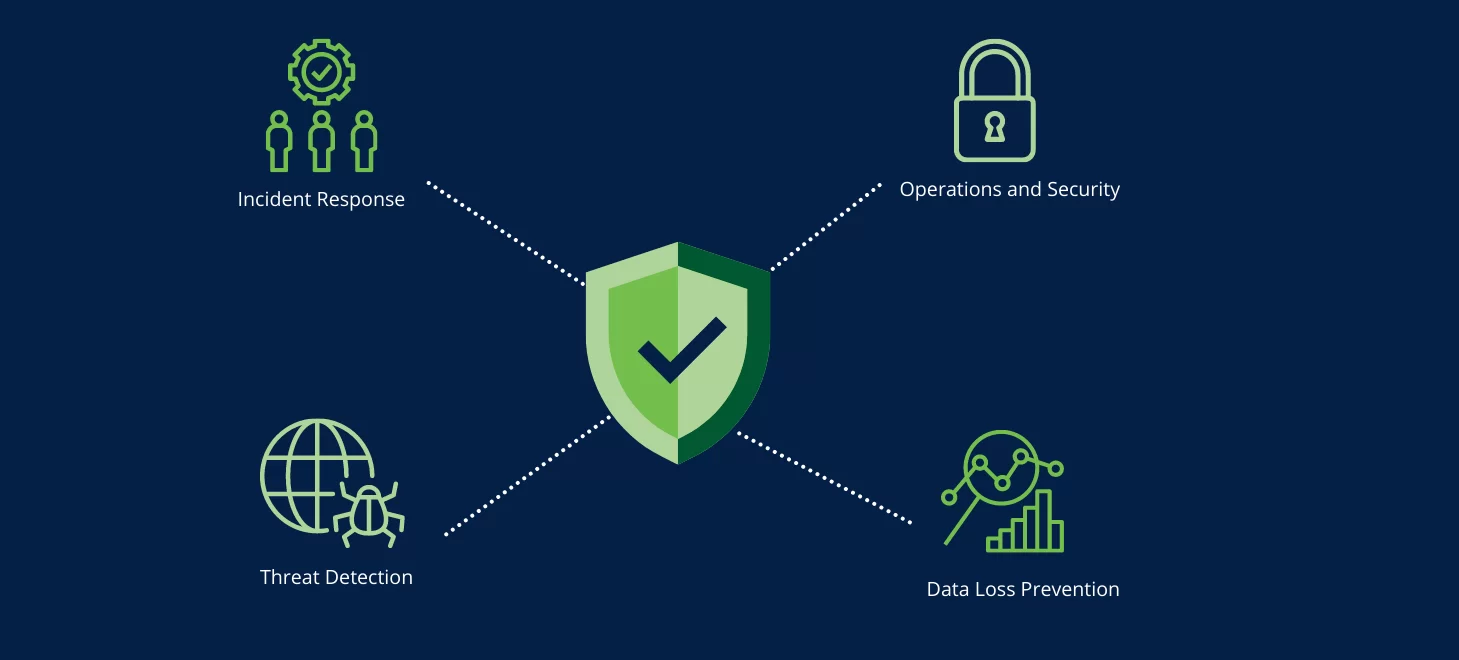
Threat Detection and Response
Our threat detection and response solutions help you identify and mitigate potential security threats in real-time.
- Real-Time Monitoring: Continuously monitor systems for suspicious activities.
- Incident Response: Quickly respond to and mitigate security incidents.
Access Control and Management
Manage and control access to your systems and data with our robust access control solutions.
- User Authentication: Implement multi-factor authentication (MFA) and secure login methods.
- Role-Based Access: Define and enforce access policies based on user roles.
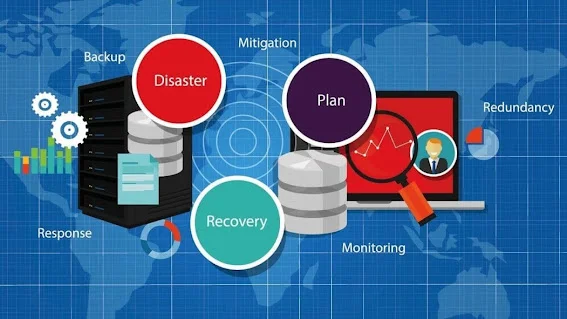
Data Backup and Recovery
Protect your data with reliable backup and recovery solutions to minimize downtime and data loss.
- Regular Backups: Schedule automated backups to ensure data is consistently protected.
- Disaster Recovery: Implement disaster recovery plans to restore data quickly in case of an incident..
Compliance and Risk Management
Ensure your data security practices comply with industry regulations and standards.
- Regulatory Compliance: Adhere to standards such as GDPR, HIPAA, and PCI-DSS.
- Risk Assessment: Conduct regular risk assessments to identify and address potential vulnerabilities.
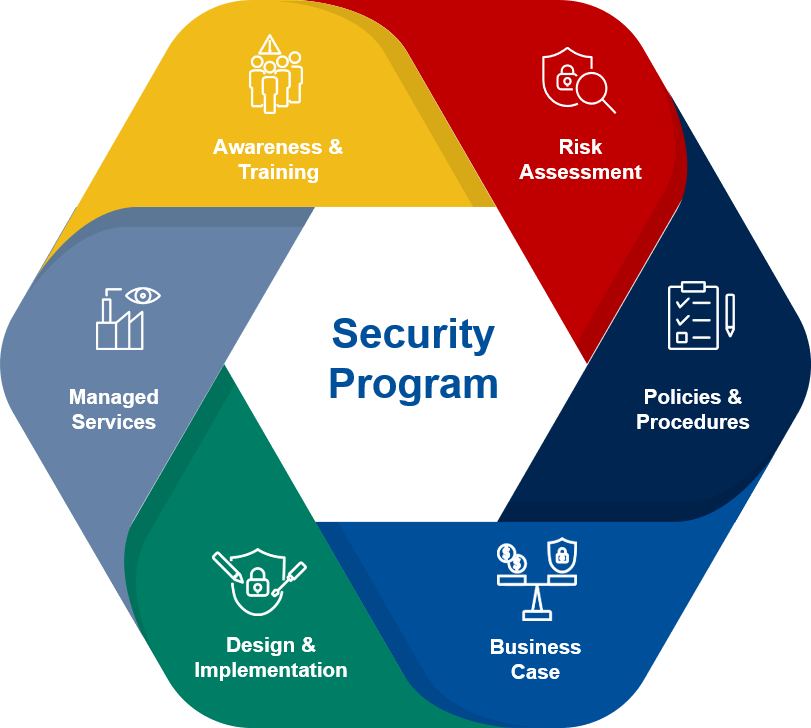
Security Audits and Assessments
Regularly review and assess your security measures to ensure they are effective and up-to-date.
- Audits: Perform thorough audits to evaluate the effectiveness of your security policies and controls.
- Vulnerability Assessments: Identify and address vulnerabilities in your systems and applications.
Employee Training and Awareness
Educate your employees on best practices and potential threats to enhance your organization’s overall security posture.
- Security Training: Provide training sessions on security best practices and awareness.
- Simulations: Conduct phishing simulations to test and improve employee responses to potential threats.
Network Security Solutions
Implement comprehensive network security measures to protect your infrastructure from external and internal threats.
- Firewall Protection: Deploy advanced firewalls to block unauthorized access and malicious traffic.
- Intrusion Detection Systems: Monitor and respond to potential intrusions and network anomalies.
